In crypto, identity is often expected to be anonymous, allowing users to transact without revealing their real-world identities.
Yet, even though these identities remain anonymous, transparency is upheld as all transactions are publicly traceable. One crucial component enabling this anonymity is decentralised identity, which we’ll explore in this article.
What is Decentralised Identity?
A decentralised identity is an approach to identifying and authenticating users without relying on centralised authority systems.
In traditional systems, identity management is centralised, with user data stored in a single database, typically managed by governments or corporations.
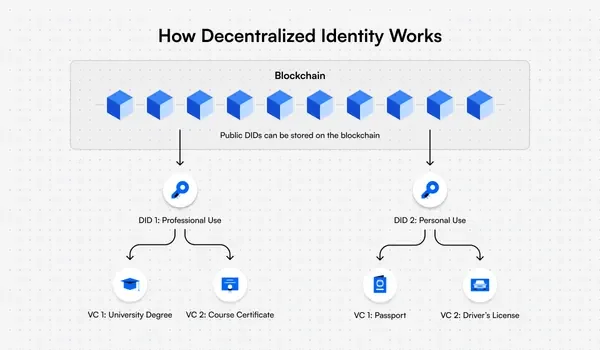
Source: Dock.io
Data such as names, birth dates, identity numbers, and even email addresses are used to verify users when they engage with online services.
In centralised systems, a single authority is responsible for managing and securing user identities, but this approach is vulnerable to cyberattacks or hacking, as all the data is stored in one place.
If that database is compromised, every user’s data could be exposed. This is where decentralised identity steps in as a solution.
Decentralised identity allows users and organisations to manage their identities using a distributed approach.
Rather than relying on central identity providers, decentralised systems use distributed ledger technology (DLT) like blockchain to store information in a digital wallet.
What is the Purpose of Decentralised Identity?
The main advantage of decentralised identity is the security and full control it grants users over their data.
In centralised systems, users have little control over who can access their information. Their data could be misused or even sold without their knowledge. In contrast, decentralised systems allow users to choose what information they share with each service.
Another benefit is that decentralisation eliminates the single point of failure—the weak spot where all data is stored in one place.
In this system, an attack on a single node does not mean all users’ data is accessible. This strengthens cybersecurity and offers better privacy protection for users.
For example, decentralised identity systems enable users to log into various services without needing to share credentials or passwords.
Users can simply verify themselves through their digital wallet, which they manage independently, without the involvement of a central authority.
How is Decentralised Identity Created?
To create a decentralised identity, users can use specialised platforms that allow them to issue a unique identity. This identity can then be used across multiple platforms.
Blockchain technology, which supports the concept of self-sovereign identity, enables every user to have complete control over their digital identity.
This system integrates blockchain with digital identities, reducing reliance on third parties.
The identity is stored on decentralised networks like the InterPlanetary File System (IPFS), giving users full control over their data and ensuring it cannot be accessed or shared without their consent.
Source: ENS
For instance, the Ethereum Name Service (ENS) lets users create a ‘.eth’ domain to replace their long and hard-to-remember wallet addresses.
Additionally, non-transferable non-fungible tokens (NFTs) called soulbound tokens can represent a person’s identity and achievements in the Web3 world.
Benefits of Decentralised Identity
One of the biggest benefits of decentralised identity is enhanced privacy and security.
Users no longer need to worry about their data being misused by centralised service providers. They can decide what information they want to share and with whom.
Moreover, this system offers better protection against identity theft, cyberattacks, or hacking. An attack on a single entity won’t result in a large-scale data breach, as is often the case in centralised systems because the data isn’t stored in a single location managed by one entity.
Users also no longer need to use passwords to access services, as authentication is performed using secure cryptographic keys.
Another advantage is the flexibility of decentralised identity, which can be applied across various sectors.
From identity verification for financial services to validating educational certificates, everything can be done more securely and quickly without involving third parties.
Examples of Decentralised Identity
Many platforms now support the concept of decentralised identity. Some of the notable examples include:
- Ethereum Name Service (ENS): Helps users create ‘.eth’ domains to replace their long wallet addresses, making transactions on the Ethereum network more convenient.
- Unstoppable Domains: This platform allows users to buy and own Web3 domain names that cannot be reclaimed by any centralised entity.
- Proof of Humanity: A decentralised social verification system on Ethereum, where users can create profiles that are validated by other humans to prove their identity.
- Soulbound Tokens (SBTs): Non-transferable NFTs that represent a person’s digital identity and achievements in the Web3 space.
All these examples show that decentralised identity is not just a concept, but is already being implemented across various platforms, bringing us closer to a future where privacy and security are enhanced.
Conclusion
Decentralised identity offers a solution to the many challenges faced by centralised identity systems.
By granting users full control over their data and enhancing security through decentralisation, this system promises a future where privacy, security, and identity are better managed.
As the digital world continues to evolve, decentralised identity will become increasingly relevant, playing a key role in areas such as finance, education, and many other sectors.
With the growing adoption of blockchain technology, decentralised identity is opening up new opportunities for users to manage and protect their data in the digital world.

